User: TELMEX
Password: WEP Key default of the equipment
The possible WEP keys can be obtained by its SSID.
We have generated a script (generarrainbowtable.py) that allows us generate a rainbow table with the SSID and corresponding WEP Key of 3 Huawei OUI (001E10, 002568 y 6416F0) [This would not have been possible without the work of: hochoa@websec.mx - http://websec.mx]
The obtained SSID is then introduced to “generarlistaposibleswep.py” which queries the previously generated database and writes a file (words.txt) with the list of 768 possible WEP Keys (words.txt) that can be introduced to tools like Brutus to make a dictionary attack.
768 possible WEP Keys are obtained because in each OUI the same SSID is repeated 256.
Thus, 256 WEP Keys * 3 OUIs = 768 WEP Keys
Example of the attack:
To obtain the SSID from a remote modem we will use the vulnerability “HUAWEI ECHOLIFE HG520C Revelation of Information” published by HKM that consists on opening the page:
http://<REMOTE IP>/Listadeparametros.html
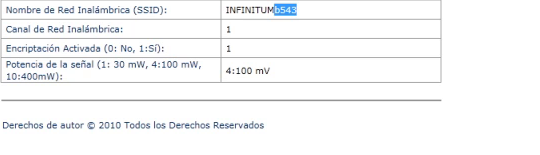
Then we introduce the obtained SSID to generarposibleswepkey.py

We configure Brutus with this list of passwords with the user “TELMEX”.

Downloads:
Generaterainbowtable.py
Generatepossiblewep.py
Generated rainbowtable:
Part 1
Part 2
Part 3
Part 4
Part 5
No comments:
Post a Comment